Where Brands & Media
Build Relationships
That Matter
-
Boost Your Media Exposure
Attract top journalists with an AI-generated press kit & brand profile, showcasing your story.
-
Instant Journalist Matches
Get matched & notified when journalists seek sources, boosting earned media & backlinks.
-
Streamlined PR Pitching Tools
Craft compelling press releases & pitches using AI, spotlighting your news effectively.
-
Sources, Brands & Products All in One Place
AI recommendations for journalists most likely to cover your story, from leading publications.
Attract top journalists with an AI-generated press kit & brand profile, showcasing your story.
Get matched & notified when journalists seek sources, boosting earned media & backlinks.
Craft compelling press releases & pitches using AI, spotlighting your news effectively.
AI recommendations for journalists most likely to cover your story, from leading publications.
Brands:
Amplify Your Media Presence
Choose your plan, setup your Brand Profile, and connect with the media in a matter of minutes. Press Hook helps you build relationships with vetted writers and editors in your industry at a fraction of traditional costs.
Boost Your Brand Exposure

Media:
Discover Top-Notch Sources
Access a curated selection of press-worthy brands and their media kits for free, all in one convenient platform. Find the perfect source precisely when you need it.
Find Quality Sources Now

Agencies:
Knock Your Clients' Socks Off
Update brand assets, send product samples to journalists, respond to media inquiries, push press releases, and pitch relevant media contacts, all in one place.
Enhance Agency PR Strategy

Press Hook in the news

Destination CRM
Dragon Glassware Catches Coverage with Press Hook

Forbes
Press Hook Makes Getting Press Coverage Easier For Your Brand

Forbes
What Brands Need To Know: Social Marketing in 2023

Fast Company
Yahoo Creators platform hits record revenue as publisher bets big on influencer-led content

PRWeek
Press Hook Adds AI Media List Generator

PRWeek
Press Hook launches AI tool to streamline journalists’ sourcing efforts
See why media, agencies & brands
love Press Hook


Recent Press in the Press Hook Community
Join Now
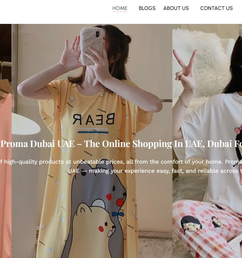
BuzzFeed // DRAGON GLASSWARE®
Jul 15, 2025

The Kitchn // Hast
Jul 10, 2025

Daily Mail // Levoit
Jul 07, 2025

Food Network // Culture Pop Soda
Jul 07, 2025